1.下载并安装Tor
在Parrot中或Kali中直接用apt安装
apt-get update && apt-get install tor2.下载并安装obfs4
apt-get install obfs4proxy3.配置Tor Bridges
在Parrot中的配置文件:
SocksPort 9050
SocksListenAddress 127.0.0.1:9050 #为SOCKS代理地址
ClientOnly 1
#VirtualAddrNetwork 10.192.0.0/10
DNSPort 53
DNSListenAddress 127.0.0.1
AutomapHostsOnResolve 1
AutomapHostsSuffixes .onion,.exit
TransPort 9040
TransListenAddress 127.0.0.1
Log notice file /var/log/tor/notices.log
RunAsDaemon 1
ClientTransportPlugin obfs4 exec /usr/bin/obfs4proxy managed
UseBridges 1
Bridge obfs4 194.132.208.5:30581 7ED2B054B0E265BC10E3E277F4C0093455E87181 cert=Jm5OAs3DNqSsrsKBFAZzbaq/c7fq9M8+mxJXAO4ohUp0xFeImzxuEJmiT1mk0hAicTw0KA iat-mode=0
Bridge obfs4 155.94.238.154:443 F90B999AF1B4A0F5EEDA2E7E131A892609D7243D cert=NRCBE4aF9XCyRs3T5f8g5gzDV+Mj4oEFHx2prmSrz6vOni4H9BIxGSMIH6KK6H1SMATCEw iat-mode=0
Bridge obfs4 209.141.35.221:33965 A5BE53F078FC472002791D8C037D189EDEB6DE06 cert=jlzZIUA1z7ILTpUsgliL4ulissYmolqKxufObRQiObe0wPDYtPsDxuRrlr/r/QLwrgg+Vw iat-mode=0其中网桥需要bridges@torproject.org发送邮件申请,其主题和内容为get transport obfs4,obfs4可换成其他类型网桥。
4.重启Tor
service tor restart成功连接网桥之后可看到notices.log中有详细的信息:
Jun 18 23:02:15.000 [notice] Interrupt: exiting cleanly.
Jun 18 23:02:16.000 [notice] Tor 0.2.9.11 (git-572f4570e1771890) opening log file.
Jun 18 23:02:16.225 [warn] OpenSSL version from headers does not match the version we're running with. If you get weird crashes, that might be why. (Compiled with 1010006f: OpenSSL 1.1.0f 25 May 2017; running with 1010005f: OpenSSL 1.1.0e 16 Feb 2017).
Jun 18 23:02:16.242 [notice] Tor 0.2.9.11 (git-572f4570e1771890) running on Linux with Libevent 2.0.21-stable, OpenSSL 1.1.0e and Zlib 1.2.8.
Jun 18 23:02:16.242 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://www.torproject.org/download/download#warning
Jun 18 23:02:16.242 [notice] Read configuration file "/usr/share/tor/tor-service-defaults-torrc".
Jun 18 23:02:16.242 [notice] Read configuration file "/etc/tor/torrc".
Jun 18 23:02:16.245 [warn] The SocksListenAddress option is deprecated, and will most likely be removed in a future version of Tor. Use SocksPort instead. (If you think this is a mistake, please let us know!)
Jun 18 23:02:16.245 [warn] The DNSListenAddress option is deprecated, and will most likely be removed in a future version of Tor. Use DNSPort instead. (If you think this is a mistake, please let us know!)
Jun 18 23:02:16.245 [warn] The TransListenAddress option is deprecated, and will most likely be removed in a future version of Tor. Use TransPort instead. (If you think this is a mistake, please let us know!)
Jun 18 23:02:16.245 [notice] Opening Socks listener on 127.0.0.1:9050
Jun 18 23:02:16.245 [notice] Opening DNS listener on 127.0.0.1:53
Jun 18 23:02:16.245 [notice] Opening Transparent pf/netfilter listener on 127.0.0.1:9040
Jun 18 23:02:16.000 [notice] Parsing GEOIP IPv4 file /usr/share/tor/geoip.
Jun 18 23:02:16.000 [notice] Parsing GEOIP IPv6 file /usr/share/tor/geoip6.
Jun 18 23:02:16.000 [notice] Bootstrapped 0%: Starting
Jun 18 23:02:16.000 [notice] Delaying directory fetches: No running bridges
Jun 18 23:02:16.000 [notice] Signaled readiness to systemd
Jun 18 23:02:17.000 [notice] Opening Control listener on /var/run/tor/control
Jun 18 23:02:18.000 [notice] Bootstrapped 5%: Connecting to directory server
Jun 18 23:02:18.000 [notice] Bootstrapped 10%: Finishing handshake with directory server
Jun 18 23:02:19.000 [notice] Bootstrapped 15%: Establishing an encrypted directory connection
Jun 18 23:02:19.000 [notice] Bootstrapped 20%: Asking for networkstatus consensus
Jun 18 23:02:19.000 [notice] Bridge 'Unnamed' has both an IPv4 and an IPv6 address. Will prefer using its IPv4 address (155.94.238.154:443) based on the configured Bridge address.
Jun 18 23:02:19.000 [notice] new bridge descriptor 'Unnamed' (fresh): $F90B999AF1B4A0F5EEDA2E7E131A892609D7243D~Unnamed at 155.94.238.154
Jun 18 23:02:19.000 [notice] I learned some more directory information, but not enough to build a circuit: We have no usable consensus.
Jun 18 23:02:21.000 [notice] Bootstrapped 25%: Loading networkstatus consensus
Jun 18 23:02:34.000 [notice] I learned some more directory information, but not enough to build a circuit: We have no usable consensus.
Jun 18 23:02:34.000 [notice] Bootstrapped 40%: Loading authority key certs
Jun 18 23:02:35.000 [notice] Bootstrapped 45%: Asking for relay descriptors
Jun 18 23:02:35.000 [notice] I learned some more directory information, but not enough to build a circuit: We need more microdescriptors: we have 0/7216, and can only build 0% of likely paths. (We have 0% of guards bw, 0% of midpoint bw, and 0% of exit bw = 0% of path bw.)
Jun 18 23:02:35.000 [notice] Bootstrapped 50%: Loading relay descriptors
Jun 18 23:03:52.000 [warn] Rejecting request for anonymous connection to private address [scrubbed] on a TransPort or NATDPort. Possible loop in your NAT rules?
Jun 18 23:04:09.000 [notice] Bootstrapped 57%: Loading relay descriptors
Jun 18 23:04:09.000 [notice] Bootstrapped 64%: Loading relay descriptors
Jun 18 23:04:09.000 [notice] Bootstrapped 74%: Loading relay descriptors
Jun 18 23:04:09.000 [notice] Bootstrapped 80%: Connecting to the Tor network
Jun 18 23:04:10.000 [notice] Bootstrapped 90%: Establishing a Tor circuit
Jun 18 23:04:12.000 [notice] Tor has successfully opened a circuit. Looks like client functionality is working.
Jun 18 23:04:12.000 [notice] Bootstrapped 100%: Done
Jun 18 23:04:27.000 [warn] Proxy Client: unable to connect to 209.141.35.221:33965 ("general SOCKS server failure")
Jun 18 23:04:27.000 [warn] Proxy Client: unable to connect to 194.132.208.5:30581 ("general SOCKS server failure")
Jun 18 23:08:55.000 [warn] Rejecting request for anonymous connection to private address [scrubbed] on a TransPort or NATDPort. Possible loop in your NAT rules? [337 similar message(s) suppressed in last 300 seconds]其中的proxychains是默认有9050端口代理的,如果没有在/etc/proxychains.conf中添加:
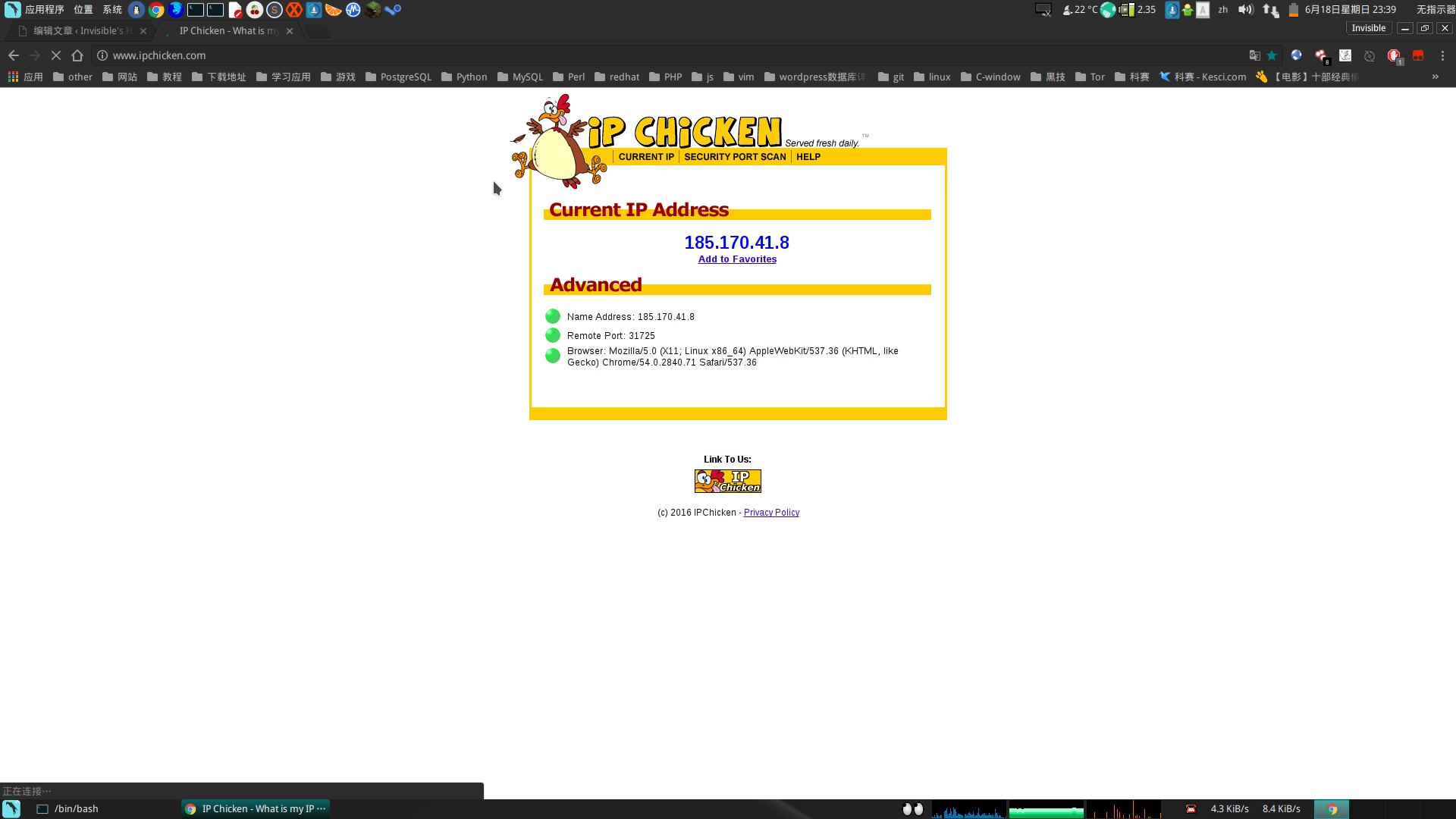
socks4 127.0.0.1 9050最后使用proxychains启动火狐浏览器,直接使用Tor代理上网,也可在Chrome中的SwitchySharp设置IP为127.0.0.1、端口为9050的SOCKS代理
proxychains fixefor